The Top 30 Worst Cyberattacks in History
Introduction
Cyberattacks shape the modern economy. They halt services, lock up data, and force costly rebuilds. Some events spread in hours across the world. Others sit quietly for months inside trusted software and suppliers. Ranking the “worst” is not simple.
Damage takes many forms. There is direct loss, long cleanup, and hidden business impact. This article solves that by listing a Top 30 for scope and context. Then it explains the Top 10 in detail based on the best available damage estimates.
You will find all 30 incidents in a table. You will also see a chart that compares the Top 10 by estimated damages in U.S. dollars. The goal is simple. Learn what happened. See the scale. Take away clear lessons you can use today.
Methodology
This list focuses on global reach, financial cost, and real-world disruption. We used widely cited public estimates in U.S. dollars when possible. Many figures vary by source. Cyber incidents often have indirect costs that are hard to count. When credible numbers do not exist, the table shows “N/A.”
Some entries are famous for strategic impact rather than a clean dollar amount. That still matters. A power grid outage or a supply-chain breach can change national policy, even when the price tag is unclear.
The table includes year, attack or operation name, primary targets, attack type, and estimated damages. The chart shows the Top 10 by damages only. This keeps the visual simple and useful.
The Top 30 At A Glance (Table)
We prepared a full, spreadsheet-style Top 30 Worst Cyberattacks table for you. It includes the year, the operation name, key targets, the type of attack, and the best known or most cited damage totals in USD.
| Ranking | Year | Attack/Operation | Primary Target(s) | Attack Type | Damages (USD Billions) |
|---|---|---|---|---|---|
| 1 | 2020 | SolarWinds Supply-Chain Espionage | U.S. agencies; global firms | Supply-chain espionage | 100 |
| 2 | 2004 | Mydoom Email Worm | Global internet users | Worm | 38.5 |
| 3 | 2003 | Sobig Worm | Global Windows systems | Worm | 30 |
| 4 | 2001 | Klez Email Worm | Global Windows users | Worm | 19.8 |
| 5 | 2000 | ILOVEYOU Email Worm | Global Windows users | Worm | 15 |
| 6 | 2017 | NotPetya Wiper | Maersk; Merck; TNT; others | Wiper/Ransomware | 10 |
| 7 | 2023 | MOVEit Mass Exploitation | Hundreds of organizations | Data theft via zero-day | 10 |
| 8 | 2017 | WannaCry Ransomware | NHS; global enterprises | Ransomware | 4 |
| 9 | 2024 | Change Healthcare Ransomware | U.S. healthcare payments | Ransomware | 3.1 |
| 10 | 2001 | Code Red Worm | Microsoft IIS servers | Worm | 2.6 |
| 11 | 2010 | Stuxnet Industrial Sabotage | Iran’s Natanz facility | Industrial control malware | N/A |
| 12 | 2014 | Sony Pictures Hack | Sony Pictures Entertainment | Destructive breach | 0.1 |
| 13 | 2016 | Bangladesh Bank SWIFT Heist | Bangladesh Bank | Cyber heist | 0.081 |
| 14 | 2021 | Colonial Pipeline Ransomware | Colonial Pipeline | Ransomware | N/A |
| 15 | 2013–2014 | Yahoo Mega Breaches | Yahoo | Data breach | 0.35 |
| 16 | 2018 | Marriott/Starwood Breach | Marriott International | Data breach | N/A |
| 17 | 2013 | Target Breach | Target | Point-of-sale malware | 0.292 |
| 18 | 2014 | Home Depot Breach | Home Depot | Point-of-sale malware | 0.179 |
| 19 | 2015 | Anthem Breach | Anthem (Blue Cross) | Data breach | N/A |
| 20 | 2015 | OPM Federal Data Breach | U.S. Office of Personnel Management | Data breach | 0.24 |
| 21 | 2015 | Ukraine Power Grid Attack | Ukrainian utilities | Grid cyberattack | N/A |
| 22 | 2007 | Estonia DDoS Attacks | Govt; banks; media | DDoS | N/A |
| 23 | 2016 | Dyn/Mirai DDoS | Dyn DNS; major sites | IoT botnet DDoS | N/A |
| 24 | 2011 | RSA SecurID Breach | RSA (EMC) | Supply-chain/credential | N/A |
| 25 | 2021 | JBS Ransomware | JBS (meat processing) | Ransomware | 0.011 |
| 26 | 2022 | Ronin Bridge Hack | Sky Mavis / Axie Infinity | Crypto heist | 0.62 |
| 27 | 2021 | Poly Network Hack | Poly Network | Crypto heist | 0.611 |
| 28 | 2018 | Coincheck Hack | Coincheck (Japan) | Crypto heist | 0.53 |
| 29 | 2014 | Mt. Gox Hack/Collapse | Mt. Gox | Crypto heist | 0.47 |
| 30 | 2011 | Sony PlayStation Network Breach | Sony | Data breach | N/A |
Deep Dive: The Top 10 Worst Cyberattacks By Estimated Damages
Below are the Top 10 by estimated cost. The impact notes focus on what broke, why it spread, and what we learned.
1) SolarWinds Supply-Chain Espionage (2020) — Estimated Up To ~$100 Billion

Attackers placed a backdoor inside a routine update of a popular IT management platform. Many U.S. federal agencies and major companies trusted that software. The tainted update moved through normal channels and reached thousands of networks. The breach lasted for months before detection.
The cost came from incident response, legal work, system rebuilds, audits, and long policy changes. It also drove expensive supplier checks and architecture shifts. The lesson is clear. Treat every supplier as part of your attack surface. Verify updates. Segment management tools. Monitor behavior, not just signatures.
2) Mydoom Email Worm (2004) — ~$38–38.5 Billion

Mydoom spread through email at record speed. It forged sender names and tricked users into opening an attachment. It then copied itself to new targets and flooded networks. Firms faced clogged mail servers and slow systems for days. Cleanup took time and labor across the world.
Mydoom shows the cost of small actions at scale. A single click in many places created a storm. Email security, user training, and attachment controls reduce this risk. So do sandbox checks and link isolation.
3) Sobig Worm (2003) — ~ $30 Billion
Sobig, especially the F variant, blasted email systems and network links in 2003. It turned infected PCs into spam engines and opened doors for remote control. It caused service outages and heavy loss of work time. Many firms had to shut systems and clean by hand, one machine at a time.
Sobig proved that speed kills. Early detection and fast containment matter. Block known-bad file types. Throttle mass mail. Watch for outbound spikes that hint at botnet behavior.
4) Klez Email Worm (2001) — ~ $19.8 Billion

Klez used forged sender fields and smart tricks to slip past early filters. It mailed itself to address books and corrupted files. It also disabled antivirus tools on the host. The worm stayed active for years and forced long cleanup campaigns.
Klez set the tone for modern email threats. Identity checks and sender protection (SPF, DKIM, DMARC) help now. So do endpoint controls that stop script abuse and macro misuse. Keep those controls on every device, not just the office network.
5) ILOVEYOU Email Worm (2000) — Up To ~ $15 Billion
ILOVEYOU hit tens of millions of Windows PCs in days. A simple subject line and a VBScript attachment did the rest. It overwrote media files, stole credentials, and mailed itself to every contact. Businesses shut down mail gateways and spent weeks cleaning up.
The lesson is discipline. Block scriptable attachments. Strip active content in mail. Teach users to expect strict file rules. Prepare mass-disable playbooks for messaging services when the worst hits.
6) NotPetya Wiper (2017) — ~ $10 Billion

NotPetya looked like ransomware. In truth it was a wiper. It destroyed data and broke boot records. It spread through a poisoned update of common accounting software, then used stolen credentials and network exploits to move laterally. Global brands lost hundreds of millions each. Shipping, pharma, and logistics took heavy hits.
NotPetya is the model case for segmentation and tested restores. Build strong identity guardrails. Block unsigned scripts. Limit domain admin use. Practice bare-metal recovery. Time matters when a wiper starts.
7) MOVEit Mass Exploitation (2023) — ~ $10+ Billion

Criminals found a zero-day in a managed file transfer product. They used it to steal data from hundreds of organizations. Victims covered many sectors and countries. The follow-on costs included breach response, credit monitoring, and legal exposure. The long tail included contract reviews and supplier audits.
The lesson is to map and guard file transfer paths. Patch fast. Gate external access with strong auth and allow lists. Monitor for sudden file activity and strange compression behavior.
8) WannaCry Ransomware (2017) — ~ $4 Billion
WannaCry used a Windows SMB exploit to spread without user action. It hit hospitals, factories, rail, and telecoms. Many machines lacked patches that were already available. The UK’s National Health Service faced canceled appointments and delayed care. Paying the ransom did not help much. Keys were unreliable, and data often stayed locked.
WannaCry fixed a mindset. Patch hygiene moved from “IT task” to “business risk.” Modern controls now include network isolation, exploit mitigations, and backups with offline copies. Recovery drills need to include mass reimage steps.
9) Change Healthcare Ransomware (2024) — ~ $3+ Billion And Climbing

Change Healthcare runs key payment and claims systems across U.S. healthcare. The ransomware hit disrupted pharmacies, clinics, and hospitals. Providers struggled to process claims and fill prescriptions. The parent company reported multi-billion costs for response, tech rebuild, and support advances to affected providers. Notifications later reached tens of millions of people.
The lesson is resilience in critical hubs. Build manual fallback for the most basic flows. Segment the most sensitive processing pipelines. Use strong identity controls to block token theft and session hijacking. Tie incident response to cash-flow continuity, not just server uptime.
10) Code Red Worm (2001) — ~ $2.6 Billion

Code Red exploited a known flaw in Microsoft IIS. It defaced sites, slowed networks, and launched denial-of-service traffic. The worm spread fast and showed that web server flaws can shape global traffic in days. Cleanup and lost work time drove the bill into the billions.
The lesson is simple. Patch internet-facing services first. Use virtual patching at the edge when vendor fixes are pending. Watch for sudden spikes to unusual destinations. Block them fast.
Chart: Damages For The Top 10
We created a bar chart that compares the Top 10 incidents by estimated damages in U.S. dollars. It mirrors the order above. You can view it here:
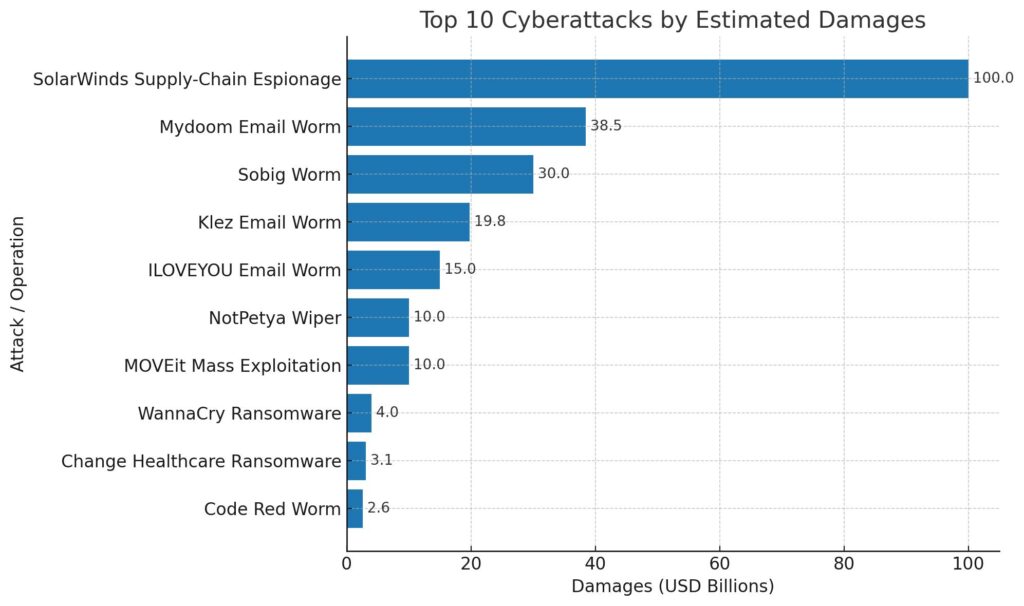
Note: Values are rounded. Some events have wide ranges. We used the most cited or conservative figure to keep the view consistent.
Conclusion
The Top 30 incidents show a clear pattern. Attacks that move through trust pathways and common tools cause the most damage. Worms that spread by themselves still matter. Ransomware now powers broad extortion. Payment hubs and healthcare systems show how cyber risk becomes a national issue within days.
Use this list as a playbook. Patch with intent. Treat suppliers as part of your own network. Segment with care. Protect backups as if they are your last line of defense. Prepare alternate workflows for core services. The worst attacks in history are not just stories. They are guides for what to fix before the next one starts.
