The CEO’s Role in Driving a Cyber-Secure Culture across the Organization
Introduction
Cybersecurity is an organizational problem with strategic implications that needs executive attention and cannot be considered solely as the domain of the IT department in the modern digital economy. Besides systems, people, business profiles, and reputations are now becoming targets of ransomware infiltrations, information leaks, and hackers’ espionage. CEOs have the overall responsibility of ensuring that cybersecurity becomes part of the company’s body of beliefs, operating practices, and decision-making because they are the custodians of the vision and culture of the company.
Cyber-secure culture consists of a shared value, not a one to gather together or comply with. This culture also affects employee information management, incident reporting, risk management, and the adoption of digital tools in the corporate world. It should be firmly embedded; with the best leaders working in the middle aiding it to become a success, and it must be supported by the top leaders, beginning with the CEO.
Developing the Cybersecurity Strategic Vision
The CEO’s primary responsibility is to integrate cybersecurity into the organization’s business plan. Cybersecurity is an ongoing strategic capability that will lead to innovation, consumer trust, and company survival instead of a one-time technology project.
To ensure this strategy, the CEO should incorporate cyber and other strategic risks, such as operational, financial, and reputational risks. The CEO should ensure that the cyber risk is factored into the company’s expansion strategy, such as when the insurance company might expand to new geographical locations or offer new digital services.

Cybersecurity issues should be part of the board-level strategic planning sessions and meetings of IT/ risk committees. It also implies linking cybersecurity investments with strategic outcomes, such as better regulatory compliance, a faster time to market of safe products, or reduced business disruption.
Investing in Infrastructure and Innovation
It is also essential to put in place a security culture, including allocating resources and tools. CEOs ensure that a company invests in the latest, scalable, and safe technology that prevents, detects, and corrects cyberattacks.
Such investments may include:
⦁ Safe endpoint protection tools
⦁ Cloud security services and secure configurations
⦁ Intrusion Detection Systems (IDS) and Firewalls
⦁ Secure software development practices
⦁ Encryption of data when it is in transit and at rest
⦁ Identity and access management (IAM) platforms
Besides defensive strategies, the CEO should promote security innovation. By using behavioral analytics to support the detection of insider threats, some of the damage may be prevented, and the adoption of threat detection systems with the help of AI may make their work more effective.
CEOs must also learn that these expenses represent the pillars of business continuity and digital trust and are not sunk costs.
Making Employee Awareness and Training a Priority
The most common cybersecurity weak point is the workers, not because they are irresponsible, but because they are ignorant. A Chief Executive Officer concerned about cybersecurity training would make it crucial for everybody.

However, e-learning programs focusing on compliance alone are not enough for training. The CEO needs to make sure that the instruction is:
⦁ Captivating and interactive through scenarios, simulations, and gamified tests.
⦁ Communicative and continuously adaptive, with changes based on emerging threats.
⦁ Role-specific, such as software developers, HR, and finance, are facing different risks.
⦁ Some of its metrics include the reporting frequency and the rate at which phishing succeeds.
Moreover, the CEO could assign cybersecurity champions or ambassadors to other departments to support advancing best practices throughout their teams. This way, the awareness is decentralized, but security becomes a team goal, rather than a rulebook.
⦁ Engaging Ecosystem/ External Stakeholders
The organization does not work in isolation. The suppliers, contractors, cloud companies, and vendors all contribute to the risks of cyberattacks. The CEO is responsible for handling the company’s external security.
It comprises;
⦁ Third-party risk assessments
⦁ Incorporating stipulations related to cybersecurity in vendors’ contracts
⦁ Insisting on the security rules among partners
⦁ Attending cybersecurity conferences and intelligence sharing networks specializing in the industry
In addition, regulatory pressure is increasing around the world. It is the task of the CEO to ensure that the company complies with both domestic and foreign policies related to cybersecurity disclosures as per US SEC regulatory requirements, GDPR, NIS2, and HIPAA.
In a cyber-disaster and its wake, it is the role of the CEO to ensure the communication channels with the authorities, consumers, and the partners in the industry are open – this builds confidence and illustrates corporate responsibility.
Putting Governance and Accountability Frameworks in Place
Responsibility transforms the strategy into governance. CEOs should have institutionalized cybersecurity governance in the organizational structure to ensure that roles, duties, and reporting relationships are beyond any doubt. It is done by creating cross-functional cybersecurity oversight where key stakeholders in the operations, finance, legal, IT, and compliance actively collaborate in determining risks and tracking mitigation efforts (Cybersecurity, 2014).
The CEO must also ensure that the board and the leadership are continuously informed about cybersecurity metrics, the number of attacks, the time to address the vulnerabilities, the outcome of the phishing simulations, and so on.
Most importantly, there should be trickle-down accountability. All the department heads should learn the implications of cybersecurity on their department. For example, the marketing team should mitigate the brand risk of social engineering attacks, the finance team should prevent safe payment processing and detection of fraud, and the human resources team should check the background and onboard such employees.
By formalizing these governance systems, the chief executive officer ensures that they elevate cybersecurity into the organization’s operations and do not treat it as a separate problem.
⦁ Leading by example: Positive Tone
Values of an organization are influenced by what the leaders of an organization say and do. Whenever a CEO takes cybersecurity seriously, other organization members receive an overwhelming message. Nevertheless, this leadership cannot be done alone through verbal boosting.
As an example, it will be portrayed as humble and committed when a CEO and employees join in an exercise in cybersecurity training. If the CEO takes the initiative to have an encrypted phone when traveling, has their business devices encrypted, uses multi-factor authentication (MFA), and encourages their workers to communicate securely, such as through encrypted email, it would make a difference as others would follow suit.
The CEO’s response during the incident is also important. It is because a CEO who will help them create a no-blame culture within the company will enable the team to develop a psychologically secure environment in which to carry out cybersecurity activities, without fear of any punishment when exposing potential risks.
Also, a proactive CEO ensures that the issue of cybersecurity is not addressed only when a failure happens. Cybersecurity awareness must be incorporated into the company’s usual rhythm through employee appreciation programs, strategy refresh, and quarterly check-ups.
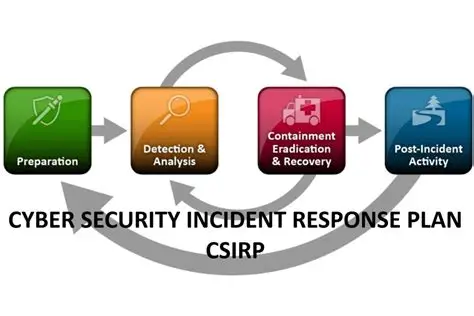
⦁ Incident Response and Crisis Preparedness
During a crisis, the culture of cybersecurity is put to the test to the very end. In most cases, the response level and subsequent breach impact are defined by a response’s speed, clarity, and honesty. The organization, with the leadership of the CEO, should develop and train a formal incident response plan (IRP). It contains:
⦁ Representative to the consumers, regulators, and media
⦁ Technical, legal, and compliance groups with evident pathways of escalating
⦁ Being aware of whom to call in case of an incident, both internally and externally
⦁ Preparation of templates for data breach notifications that should be used immediately